How to prevent damage to ransomware that is sophisticated?
Main damage caused by ransomware attack
For example, if the client PC used by the employee receives a ransomware attack, the internal data will be encrypted and the file will not be opened, and in the worst case, the PC will not be able to start up.Therefore, the business execution will be greatly delayed until the PC is restored.
If the server is attacked, it will cause more serious and wider damage.For example, if the data on the file server is encrypted, you will not be able to use any documents or form files used in business, and if the mail server data is encrypted, you will not be able to send and receive emails at all.。
If the data of the Active Directory domain controller is encrypted, other terminals participating in the domain may not be able to log in to the internal network.
Also, restoring the encrypted data takes a lot of cost and time, and if the work is stopped during that time, it will greatly lose money.Even if the system is finally restored and the work is resumed, it will be a lot of cost and effort to strengthen security measures and explain to each other and apologize.In some cases, you may be damaged, such as loss of credit, falling stock prices, and suspension of transactions.
What are the features seen in recent ransomware attacks?
Of course, security technology to prevent ransomware attacks is improving year by year, and it is actually improving the effect.However, the attacker is also launching new attack methods one after another, and the attacker and defense side offers a pretend to play.
For example, recently, "Ransomware as a Service), which undertakes the support of ransomware attacks as a cloud service such as SaaS, has been used more often.With this RAAS, you can easily launch an attack without the skills to develop ransomware, and you will be undertaken to collect ransom and the instructions of the attack method, so the hurdle of ransomware attack has been reduced at a stretch.rice field.
In addition to simply encryption of data, the number of "double intimidation" that threatens important data and flicker its publication has increased.There are some tricks for "Mie intimidation" and "quartet intimidation" that set other attacks such as telephone threats and DDOS.
By the way, it has been said that the effective measures against ransomware attacks are to properly back up the data, and to have a system that can recover data from backup even if the data is encrypted.However, in recent ransomware attacks, there are tricks that prevent data recovery by encryption of backup data and deleting backup data itself.
Furthermore, the number of attacks aiming for a wide range of infections on the entire environment, such as abusing Active Directory group policies and launching multiple devices in the network all at once.
How ransomware infects and invades
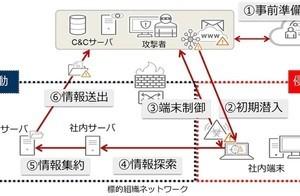
So how do ransomware infect and invade attack targets?It is a trick through emails that are often used in the past.Ransomware infection is scattered by disseminating emails with a file with a file with a file with a program that downloads ransomware, or a URL of an unauthorized site that downloads such files.
In addition, many companies have changed to the network environment, such as changing firewall settings and increasing VPN devices to improve teleworking environments since Corona's evil, but inadequate settings due to incomplete firewalls and network equipment.There are many cases where sex is exposed.The attacker finds the vulnerabilities and security holes that have caused this, and pokes cleverly.
In addition, the network environment of home from home is considerably vulnerable compared to corporate networks protected by various security devices, so it is still easier to be targeted by attackers.In particular, it is necessary to pay attention to cases where some USB type mobile routers and Internet contracts can be accessed directly to the terminal from the Internet side to the terminal, which is more likely to be attacked.is.
What can you do to prevent ransomware damage?
Some of the security staff of SMEs think that "the number of ransomware damage reported is not large, and there are only cases of large companies, so it has nothing to do with small and medium -sized businesses like ours."You may be there too.
However, as explained last time, even small and medium -sized enterprises are now a target of advanced cyber attacks as well as large companies.In addition, the reported ransomware damage is just a corner of the iceberg, and there are many companies that have not been signed, but have actually been severely damaged.
So, what kind of measures should be taken to protect your system from ransomware attacks?The first thing to do is to block the deficiency of the network settings that the attacker starts with infection and invasion, and the vulnerability of server and network equipment.Specifically, we will check back or leaks in the settings of network devices and security products, and thoroughly apply the latest security patches to the OS and applications.
It is also extremely important to back up so that data can be restored even if the data is encrypted.In that case, it is strongly recommended that you keep not only online backups but also offline backups so that the backup data is not encrypted or deleted by ransomware attack.
Sawamura intelligence
さわむら とものりCyber Liezen Japan Co., Ltd. Senior Security Advisor
警察庁にてデジタルフォレンジックやサイバー攻撃対策の業務に10年従事した後、サイバーリーズン・ジャパン株式会社に入社。 現在は、サイバー攻撃や脅威情報のリサーチ、サイバーセキュリティ管理体制の高度化に係る教育や支援などを担当。これまでに、大手製造業などの多数のインシデント対応に携わっている。この著者の記事一覧はこちら